News
IEEE Journal Features Research by SDSC Internet Experts
Published August 17, 2004
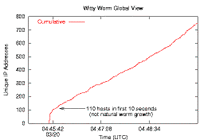
Internet worm infections typically grow exponentially in their early stages, and then gradually level off. But the Witty Worm was activated in more than 100 computers within the first 30 seconds of its outbreak, indicating that the perpetrator either used a list of vulnerable targets or triggered the release of the worm on previously hacked machines. After the first minute, Witty followed an exponential growth curve typical of other worms. 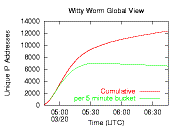
The number of infected, active machines (green line) stabilized within 45 minutes, because most of the vulnerable computers on the Internet had been compromised. After that point, restarting infected machines (with newly assigned dynamic IP addresses) caused the running total of infection addresses (red line) to continue to rise. Nearly all of the computers running software from Internet Security Systems were compromised, approximately 12,000 hosts. |
The theme of the July/August 2004 issue of IEEE Security & Privacy is "Attacking Systems," and the CAIDA study of the Witty Worm is a keynote example for other articles in the journal. In the introduction to the magazine, Associate Editor in Chief Marc Donner points out that Shannon and Moore note "the key point is that, 'the patch model for Internet security has failed spectacularly.... When end users participating in the best security practice that can be reasonably expected get infected with a virulent and damaging worm, we must reconsider the notion that end-user behavior can solve or even effectively mitigate the malicious software problem ....' So now what?" Other articles in the journal attempt to resolve that problem, but success may be elusive.
"Witty was the first widespread Internet worm to carry a destructive payload," Shannon said. "It was first in other respects, too. It was the first worm to directly attack a security product, a newly discovered vulnerability in software that was supposed to reduce a computer's vulnerability to attacks; unlike many other worms it didn't exploit a flaw in the operating system. And our research showed that it had been launched by ten times as many pre-planned infection sites as any previous worm. We suspect that in the future we will see worms with other 'firsts,' and we're not looking forward to those at all."
Shannon and Moore are senior security researchers on the Internet Telescope project of the Cooperative Association for Internet Data Analysis ( CAIDA), a program at SDSC that creates tools and technologies for Internet measurement, traffic analysis, and network topology visualization for use by network engineers and researchers. The two researchers used the CAIDA/UCSD Network Telescope, which detects remote network security events such as denial-of-service attacks, Internet worm infections, and network scanning. In the case of the Witty Worm, the Network Telescope detected messages sent by compromised computers attempting to infect other machines on the Internet.
The full article is available on the IEEE website, at http://www.computer.org/security/v2n4/mal.htm. A technical paper by Shannon and Moore that appeared immediately after the Witty Worm outbreak is available to the public on the CAIDA website, and a summary article is available from SDSC.

